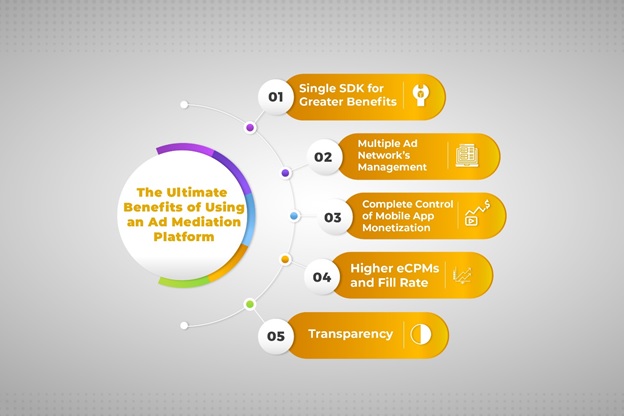
Cryptanalysis Unveiled: Definitions, Techniques, and Beyond
Cryptanalysis: From Buzzwords to Breakthroughs
Ever wondered how a hacker can crack a secret password or unlock a treasure hidden in a giant puzzle? That’s the heart of cryptanalysis—the art of sniffing out secrets in ciphers that were meant to be impenetrable. Let’s dive into the basics, the motives behind it, and the tricks that every code‑breaker uses.
What is Cryptanalysis?
In plain English, cryptanalysis is the study of breaking cryptographic systems—those fancy math tricks that keep our messages safe. Think of it as a detective story where the clues are numbers and letters, and the mystery is the original message that the system tries hard to hide.
Web-Style Take on Cryptanalysis
When we talk about the web of cryptanalysis, we’re looking at how these methods play out online. From online banking to secure messaging apps, cryptanalysis can happen in the background when someone tries to sniff big data packets, juggle HTTP requests, or even sniff Wi‑Fi traffic. It’s all about finding that weak spot—whether it’s a bad implementation, a predictable key, or a side‑channel leak.
Why Bother? The Goals of Cryptanalysis
- Security Audits: Test the robustness of encryption before it actually protects your data.
- Discovering Vulnerabilities: Spot flaws that could be exploited by real attackers.
- Academic Exploration: Push the limits of math and computer science.
- Legal & Forensic Use: Help law enforcement read encrypted evidence when necessary.
- Improving Encryption: Feed feedback into better, stronger algorithms.
Tools of the Trade: Methods of Cryptanalysis
- Brute Force: Trying every possible key until the treasure pops out. Slow, but inevitable if the password’s short.
- Dictionary Attacks: Using a pre‑compiled list of common words or phrases. Think “password‑123” falls into this.
- Statistical Attacks: Sneak a peek at frequency patterns in ciphertext to guess the alphabet. Hacker’s version of a traffic‑jam radar.
- Side‑Channel Analysis: Watching the device’s ‘heartbeat’—like power consumption or timing—to infer secrets.
- Mathematical Breakthroughs: Employing the latest number theory tricks—like Shor’s algorithm in quantum computing—to solve big problems quickly.
Each method depends on the cipher’s design and how well it resists that particular attack. Cryptographers and attackers usually play an ever‑advancing game of one‑up‑the‑other.
Wrapping It Up
So, next time you hear about a new encryption scheme or a big security company claiming “our system is unbreakable,” remember that cryptanalysis is always ready to play the role of the challenger—looking for ways to turn the supposed fortress into a playground. The battle between making ciphers strong and breaking them weak is what keeps our digital world both safe and exciting.
Cryptanalysis Definition
Decoding the Art of Cryptanalysis
Cryptanalysis used to be all about peeking into secret messages and figuring out what grizzled spies were hiding inside them. Think of it as the secret decoder ring hobby that grew into a full‑blown science.
From Secret Code‑Sleuthing to Modern-Day Crypto‑Hunter
Today, the word “cryptanalysis” means “how to break the locks that cryptography puts up.” Whether you’re poking holes in a password scheme, testing a new encryption algorithm, or just curious about how strong a cipher really is, you’re in the business of breaking or at least understanding the protective walls set up by cryptography.
What Does It Do?
- It spies on encrypted data, looking for weaknesses.
- It tests the armor of cryptographic protocols—like a security audit for your digital vault.
- It quantifies security, giving hard numbers for things that were once “just good enough.”
Cryptography vs. Cryptanalysis: The Yin and Yang
Picture cryptography as the meticulous architect building a castle, and cryptanalysis as the bold explorer trying to find a back door. Together, they’re the two sides of the same coin—both essential to the field of cryptology.
So the next time you hear “cryptanalysis,” think of it as the adventurous detective trying to crack the code, one cunning clue at a time.
What is the web analysis of Cryptanalysis?
When Web Analysis Meets Steganography: A Quick & Fun Breakdown
Imagine you’re a detective who loves puzzles. Cryptanalysis is the classic “unlock the vault” game, where you get the key (the cryptographic content) and try to crack it. Web analysis takes the opposite approach: you start with a blank canvas and only get hints that might lead you to hidden treasure.
What’s the difference?
- Cryptanalysis – You’re handed the password‑protected file and your job is to try every trick to open it.
- Web analysis – No password, just a website that secretly hides the big secret somewhere. Your mission becomes “find the clues” rather than “break the lock.”
The Steganography Secret
Steganography’s mojo is invisibility. Think of it like a covert snack‑stashing method: the host (a webpage or a photo) looks ordinary, but underneath there’s a surprise hidden only for those who know the right secret code. The real trick? Making sure everybody else can’t even notice it’s there.
True, They Know It… But Can’t Read It
Even if a curious onlooker spots the “stego‑sneak” tricks, the real message remains locked behind layers of non‑readable noise. It’s like hiding your diary in a magnetic locker: you can see the locker, but the diary’s contents only make sense if you’ve got the right key.
Bottom Line for the Net‑Ninja
Think of web analysis as a stealthy sidekick to steganography: it starts blind, hunts for fingerprints, and only when the trail lines up does it pull out the real loot. Meanwhile, steganography stays undercover, proving that the best secrets are the ones no one even sees!
What are the Goals of Cryptanalysis?
Cracking the Crypto Code: What Attackers Aim For
When you’re dealing with encryption, what an attacker’s ultimate goal looks like depends on the type of crypto in play. In every key‑based scheme – whether it’s a secret key or a public‑private pair – the first thing anyone needs to nail is that key itself. The rest of the game starts there.
Typical Targets for Encryption Schemes
- Decrypt the ciphertext: Pull the original message straight out of the block of gibberish.
- Figure out the right plaintext: Sometimes, a ciphertext could conceivably map to two different messages. The attacker’s job is to decide the real one. If they can’t do this quickly – say, not in polynomial time – the system may fail to meet the semantic security standard. That’s the fancy way of saying the cipher must be “indistinguishable” from random noise to any clever snooper.
- Forge a valid ciphertext: Even without knowing what the message actually is, a cunning attacker might try to craft a plausible-looking ciphertext that the system will happily accept. That’s the classic “pump‑up” style of attack.
These points hold true for both asymmetric and symmetric cryptography. So whether your system hides secrets behind one key or patrols things with a two‑way handshake, the same fundamental battle stays the same: keys, ciphertext, plain text, and the attempt to outsmart the math that keeps them safe.
What are the methods of [Cryptanalysis]?
Cracking Codes: A Fresh Look at Cryptanalysis
Gathering All the Clues
When you’re trying to undo a cipher, the first rule is to stack every single piece of information on the table. That means:
- Public knowledge – Things that anyone can read about the cipher, like its structure or typical weaknesses.
- Reasonable guesses – Hunches that make sense given what you know about the crypto world.
- Learned insights – Clues that a savvy analyst picks up by studying the ciphertext itself or an earlier run of the system.
Sorting the Attack Playbooks
The info you gather falls into distinct “attack scenarios.” Each scenario tells you which game plan is most fruitful and tells you whether the cipher still feels safe or not. Think of it as a museum of strategies, each with its own badge of relevance.
From Manual Scripts to Machine‑Born Mystery
Before the age of computers, even the most charming cryptographers had to keep the math not too heavy. The Enigma machine, for example, was a mechanical marvel, but every part had to run smooth or the whole system would flop. Back in the day, the “algorithm” was the trickiest bit of the puzzle – simple enough that a human could set it up without mixing up the order or tossing the key letters into a hat.
When you’ve got a machine to crunch numbers, the rules loosen, but the principles don’t. No matter how fancy the hardware, the real secret lies in how well you tape together all the clues, fit them into a strategy, and turn every tiny known detail into a discovered weakness.